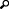- Contents
Job Manager Help
Modify a File Protection Configuration
Use the Protection - [File Protection Name] tab to modify a file protection configuration that Job Manager uses to encrypt and decrypt incoming and outgoing files.
To modify a file protection configuration
-
In the Navigation Explorer pane, click File Protections. The File Protections panel appears.
-
Do one of the following:
-
Right-click the file protection and then click File Protection Properties.
-
Double-click the file protection.
The Protection - [File Protection Name] tab appears. Job Manager includes the name of the file protection configuration in the tab name.
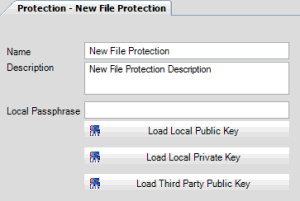
Name: Name of the file protection configuration as specified in the File Protections panel. To modify the name, rename it in the File Protections panel.
Description: Description of the file protection configuration.
Local Passphrase: Password to unlock your private key. Job Manager doesn't require you to establish a password.
Load Local Public Key: Key file that your company created. Outside parties use this key to encrypt files they send to your company.
Load Local Private Key: Key file that an outside party created. Job Manager combines this key with the outside party's public key to encrypt files your company sends to the outside party.
Load Third Party Public Key: Key file that an outside party created. Job Manager combines this key with the local private key to encrypt files your company sends to the outside party.
-
Modify the information as necessary.
-
To add the public key, click Load Local Public Key. Click the file that contains the public key and then click Open.
-
To add the private key, click Load Local Private Key. Click the file that contains the private key and then click Open.
-
To add the third-party public key, click Load Third Party Public Key. Click the file that contains the third-party public key and then click Open.
-
In the toolbar, click Save.
Note: To test the file protection configuration, see Test a File Protection Configuration.