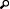- Contents
Interaction Desktop Help
Call Security
Customer Interaction Center provides call security that prevents others from listening in on a call or even determining which internal parties are involved in a conversation.
CIC administrators can configure the use of two encryption protocols to support encryption of call audio (SRTP) and call control information (TLS). This provides confidentiality and flexibility for security-sensitive organizations. Your CIC administrator can use Interaction Administrator to configure your station to use SRTP for all your calls. When SRTP is not configured for a station, the calls are “non-encrypted” or not secure from network interception.
Call Security Icons and Alerts
When the CIC administrator configures your station to request that all calls are secure or if you are involved in a call where one of the parties has requested a secure call, the CIC client monitors a call’s security level to determine if it is secure and remains secure. A call can begin as a secure (SRTP) call and later be downgraded to a non-secure state. This can occur if the secure call is transferred to, or made part of a conference with, a non-secure party.
Note: If your station is not configured to have secure calls, you do not see a lock icon at all.
-
Secure calls

A closed lock icon indicates that a call is secure within the environment controlled by CIC. It appears only if your station is configured to have secure calls and end-to-edge security
A call can be comprised of multiple audio legs. When your station is configured to have secure calls (SRTP is configured in Interaction Administrator), the call is encrypted/secured as far as possible (e.g., within the environment controlled by CIC). If all the audio legs of the call are secure to the edge of network (to another SRTP phone or to an SRTP gateway) then the closed lock icon appears, indicating a secure call. The lock does not display on an RTP station since the RTP station always has at least one non-secure audio leg (the RTP leg to the phone itself).
Note:
The Secure Call icon indicates only end-to-edge
security; i.e. security from a device configured to use TLS/SRTP and controlled
by CIC (such as your phone) to the point where CIC passes the call to
an outside agency or a device that is not configured for TLS/SRTP.
Outside agencies can include a PSTN (Public Switched Telephone Network)
or other service provider outside the control of CIC. Devices that might
not be configured for TLS/SRTP can include other telephones or a gateway
between CIC and a PSTN.
- Non-secure calls

An open lock icon indicates that at least one leg of a call is not secure. It appears only if your station is configured to have secure calls and end-to-edge security.
If your station is configured to have secure calls (SRTP is configured in Interaction Administrator), but the call cannot be made completely secure from the station to the destination (e.g., only one leg of the call is secure), and the station security level is configured for end-to-edge security, then the open lock icon appears. This means that security has been downgraded because some portion of the call cannot be encrypted, or secured. The open lock does not imply someone is listening to a call, but only that part of the call cannot be secured to prevent it from being intercepted. The open lock does not display on an RTP station, or on an SRTP station that has its security level configured as minimal. The open lock displays only on an SRTP station that has its security level configured as end-to-edge.
Note: If you point to the non-secure call icon, it displays a tooltip that explains the cause of the security alert.
-
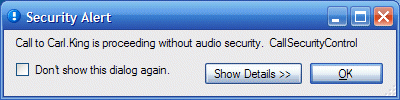
A Security Alert dialog box can also appear to alert you that the previously secure call is no longer secure.
Tip: For more information about why the call is no longer secure, click Show Details >>.
Note: If your CIC administrator grants you the right to configure your CIC client alerts, you can control whether this Security Alert dialog box appears. For more information, see Calls Configuration. When a call goes from a non-secure state to a secure state, the icon in the user’s queue changes to indicate that the previously non-secure call is now secure. You do not see a Security Alert.
Related Topics