- Contents
SSO Identity Providers Technical Reference
Troubleshooting
This section contains procedures and information for troubleshooting and correcting problems with your Customer Interaction Center Single Sign-On environment.
Single Sign-On troubleshooting tools
For troubleshooting Single Sign-On issues, Genesys recommends Fiddler by Telerik. Fiddler is a web debugging proxy that supports all major operating systems and many frameworks, such as Java, Ruby, and Microsoft .NET.
You can download Fiddler from the following website: http://www.telerik.com/fiddler
Install and configure Fiddler by following the instructions on the following website: http://docs.telerik.com/fiddler/configure-fiddler/tasks/configurefiddler
Caution!
You should allow the interception and decryption of HTTPS traffic on test
workstations only. Genesys is not responsible if you allow these activities
on a production workstation and information is exposed.
Use the Fiddler online documentation to ensure that you configure Fiddler as required for your specific CIC Single Sign-On environment, including SAML profiles and bindings.
You can then use Fiddler to capture and view web traffic for troubleshooting where the Single Sign-On configuration is failing.
Examine log files
If a CIC client application based on the .NET Framework has trouble authenticating in your CIC Single Sign-On environment, check the application logs on the Windows host computer for IceLib traces.Specifically, you want to examine entries containing class names that start with SAML2.
For the CIC server, you can view the ic_sts logs.
If you are using Microsoft Active Directory Federated Services (AD FS), you can examine the Windows Event Log for identity provider items.
Any IC Web Services errors are displayed to users in the web browser during authentication.
Updating the CIC server causes certificate validation issues
If you upgraded your CIC server from one of the following versions, the upgrade to the current version creates an incompatibility with your previous HTTPS certificates:
-
CIC 4.0 SU5
-
CIC 4.0 SU6
-
CIC 2015 R1
To correct this issue, do the following steps:
-
Open IC System Manager for the affected CIC server.
-
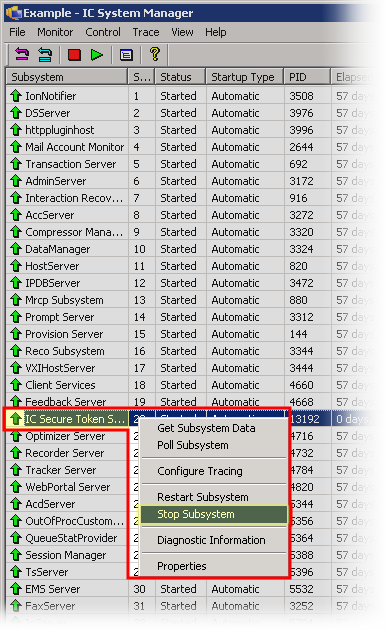
In the Subsystem column of the IC System Manager window, locate the IC Secure Token Server entry.
-
Right-click the IC Secure Token Server entry and select Stop Subsystem from the shortcut menu.
-
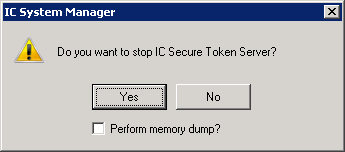
When IC Server Manager prompts you to confirm that you want to stop the IC Secure Token Server service, click Yes.
-
Wait for the IC Secure Token Server subsystem to stop, which is then indicated with a downward-pointing, red arrow.
-
On the CIC server, open a Command Prompt window as an Administrator.
-
In the Command Prompt window, navigate to the drive where the CIC server software was installed by entering and executing the following command:
D:
D: is the default drive on which the CIC server software is installed. If you installed the CIC server software to a different drive, replace D with the appropriate letter.
-
Navigate to the Default subdirectory by entering and executing the following command:
cd \I3\IC\Certificates\ICSecureTokenServer\Default
-
Rename the existing Secure Token Server HTTPS certificate by entering and executing the following command:
ren ICSecureTokenServer*.* ICSecureTokenServer*.*.backup
-
Navigate to the HTTPS subdirectory by entering and executing the following command:
cd ..\HTTPS
-
Copy the previous private key of the CIC server to the ICSecureTokenServer subdirectory by entering and executing the following command:
copy CICServerName_PrivateKey.bin ..\ICSecureTokenServer\Default\ICSecureTokenServerPrivateKey.bin
CICServerName is a variable representing the name of this CIC server.
-
Copy the previous HTTPS certificate of the CIC server to the ICSecureTokenServer subdirectory by entering and executing the following command:
copy CICServerName_Certificate.cer ..\ICSecureTokenServer\Default\ICServerTokenServerCertificate.cer
CICServerName is a variable representing the name of this CIC server.
-
Close the Command Prompt window by entering and executing the exit command.
-
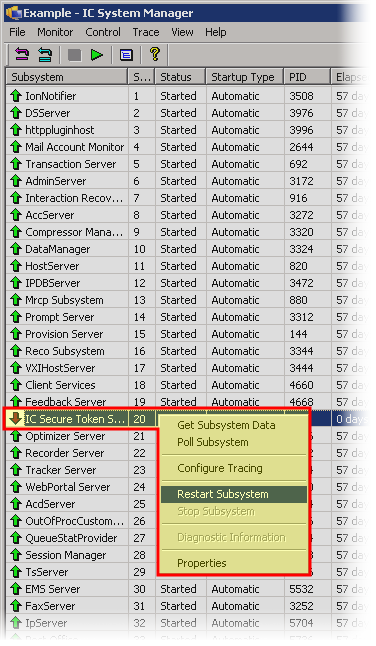
In the IC System Manager window, restart the IC Secure Token Server entry by right-clicking the entry and selecting Start from the resulting shortcut menu.
-
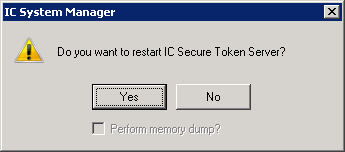
When IC Server Manager prompts you to confirm that you want to restart the IC Secure Token Server service, select the Yes button.
-
Wait for the IC System Manager window to show a green, upward-pointing arrow for the IC Secure Token Server service to indicate that it has successfully restarted.
-
Close IC System Manager.
-
Open Interaction Administrator for the CIC server.
-
In the left pane of the Interaction Administrator window, expand the System Configuration > System Sign-On container and then select the Secure Token Server item.
-
In the right pane, double-click the Configuration item.

Interaction Administrator displays the Secure Token Server Configuration dialog box.
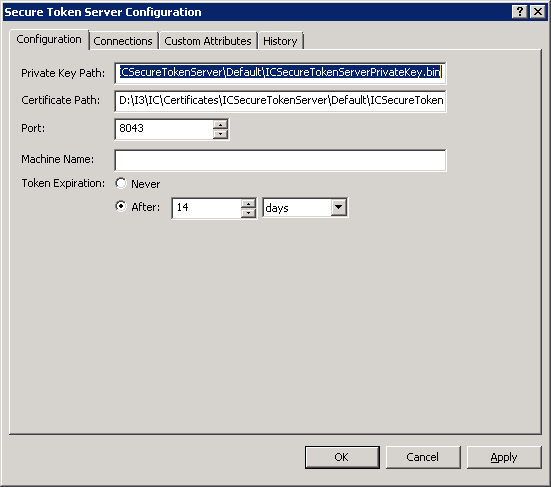
-
Ensure that the paths specified in the Private Key Path and Certificate Path boxes reference the files you created in steps 11 and 12, respectively.
-
Test a Single Sign-On logon attempt on the CIC client application to ensure that functionality has been restored.
SAML 2.0 message exchange example
This section provides an example of a standard SAML 2.0 <AuthnRequest> message and the <AuthnResponse> from the identity provider. The Secure Token Server subsystem of the CIC server expects identity providers to provide their authentication results in this type of response.
This example uses the HTTP POST binding. In this example, the identity provider uses the following URL address:
https://cic.example.com/adfs/ls/
-
The user agent accesses the Secure Token Server endpoint for authentication:
GET /SAML2WebBrowserPOSTHTTPS/login? HTTP/1.1 Host: 10.8.3.198:8043 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: keep-alive
-
The secure token server returns the SAML <AuthnRequest> message that the user agent sends to the identity provider:
HTTP/1.1 200 OK Cache-Control: no-cache, no-store Pragma: no-cache Content-Type: text/html Date: Fri, 03 Jan 2014 19:43:12 GMT Server: I3STSCore Content-Length: 1616 <html> <head> <title>SAML2WebBrowserPOSTHTTPS</title> </head> <body> Authenticating with the identity provider ... <form method="POST" action="https://cic.example.com/adfs/ls/"> <input type="hidden" name="SAMLRequest" value="PHNhbWxwOkF1dGhuUmVxdWVzdCAgICB4bWxuczpzYW1sPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6YXNzZXJ0aW9uIiAgICB4bWxuczpzYW1scD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOnByb3RvY29sIiAgICBJRD0iXzRkZjg1ODQ5YTU2MjMzNDU5YmE0YWNmNjcyZmZhNTNkIiAgICBWZXJzaW9uPSIyLjAiICAgIElzc3VlSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxMi4zMzcyNDlaIiAgICBEZXN0aW5hdGlvbj0iaHR0cHM6Ly9jbGF5Lm1pNi5jb20vYWRmcy9scy8iICAgIENvbnNlbnQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpjb25zZW50OnVuc3BlY2lmaWVkIiAgICBGb3JjZUF1dGhuPSJmYWxzZSIgICAgSXNQYXNzaXZlPSJmYWxzZSIgICAgQXNzZXJ0aW9uQ29uc3VtZXJTZXJ2aWNlVVJMPSJodHRwczovLzEwLjguMy4xOTg6ODA0My9TQU1MMldlYkJyb3dzZXJQb3N0SFRUUFMvbG9naW4iICAgIFByb3RvY29sQmluZGluZz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmJpbmRpbmdzOkhUVFAtUE9TVCIgICAgUHJvdmlkZXJOYW1lPSJodHRwczovLzEwLjguMy4xOTg6ODA0MyI+PHNhbWw6SXNzdWVyPmh0dHBzOi8vMTAuOC4zLjE5ODo4MDQzPC9zYW1sOklzc3Vlcj48L3NhbWxwOkF1dGhuUmVxdWVzdD4="/> <input type="hidden" name="RelayState" value="12f6b8be-72e9-4bb9-97a1-4392f2746ecd"/> <noscript> <p>JavaScript is disabled. Click Submit to continue.</p> <input type="submit" value="Submit"/> </noscript> </form> <script language="javascript"> window.setTimeout('document.forms[0].submit()', 0); </script> </body> </html>
The Base64 encoded SAML <AuthnRequest> message for step 2, when decoded, is as follows:
<samlp:AuthnRequest xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="_4df85849a56233459ba4acf672ffa53d" Version="2.0" IssueInstant="2014-01-03T19:43:12.337249Z" Destination=https://cic.example.com/adfs/ls/ Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" ForceAuthn="false" IsPassive="false" AssertionConsumerServiceURL="https://10.8.3.198:8043/SAML2WebBrowserPOSTHTTPS/login" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" ProviderName="https://10.8.3.198:8043"> <saml:Issuer>https://10.8.3.198:8043</saml:Issuer> </samlp:AuthnRequest>
-
The user agent posts the SAML <AuthnRequest> message to the identity provider:
POST /adfs/ls/ HTTP/1.1 Host: cic.example.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: https://10.8.3.198:8043/SAML2WebBrowserPOSTHTTPS/login? Cookie: MSISIPSelectionPersistent=aHR0cDovL0NsYXkubWk2LmNvbS9hZGZzL3NlcnZpY2VzL3RydXN0 Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 936 SAMLRequest=PHNhbWxwOkF1dGhuUmVxdWVzdCAgICB4bWxuczpzYW1sPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6YXNzZXJ0aW9uIiAgICB4bWxuczpzYW1scD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOnByb3RvY29sIiAgICBJRD0iXzRkZjg1ODQ5YTU2MjMzNDU5YmE0YWNmNjcyZmZhNTNkIiAgICBWZXJzaW9uPSIyLjAiICAgIElzc3VlSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxMi4zMzcyNDlaIiAgICBEZXN0aW5hdGlvbj0iaHR0cHM6Ly9jbGF5Lm1pNi5jb20vYWRmcy9scy8iICAgIENvbnNlbnQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpjb25zZW50OnVuc3BlY2lmaWVkIiAgICBGb3JjZUF1dGhuPSJmYWxzZSIgICAgSXNQYXNzaXZlPSJmYWxzZSIgICAgQXNzZXJ0aW9uQ29uc3VtZXJTZXJ2aWNlVVJMPSJodHRwczovLzEwLjguMy4xOTg6ODA0My9TQU1MMldlYkJyb3dzZXJQb3N0SFRUUFMvbG9naW4iICAgIFByb3RvY29sQmluZGluZz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmJpbmRpbmdzOkhUVFAtUE9TVCIgICAgUHJvdmlkZXJOYW1lPSJodHRwczovLzEwLjguMy4xOTg6ODA0MyI%2BPHNhbWw6SXNzdWVyPmh0dHBzOi8vMTAuOC4zLjE5ODo4MDQzPC9zYW1sOklzc3Vlcj48L3NhbWxwOkF1dGhuUmVxdWVzdD4%3D&RelayState=12f6b8be-72e9-4bb9-97a1-4392f2746ecd
-
The identity provider validates the user and responds with a SAML <AuthnResponse> message:
HTTP/1.1 200 OK Cache-Control: no-cache Pragma: no-cache Content-Type: text/html; charset=utf-8 Expires: -1 Server: Microsoft-IIS/7.5 X-AspNet-Version: 2.0.50727 Set-Cookie: MSISSamlRequest=; expires=Thu, 02-Jan-2014 19:43:14 GMT; path=/adfs/ls Set-Cookie: MSISAuthenticated=MS8zLzIwMTQgNzo0MzoxNCBQTQ==; path=/adfs/ls; secure; HttpOnly Set-Cookie: MSISLoopDetectionCookie=MjAxNC0wMS0wMzoxOTo0MzoxNFpcMQ==; path=/adfs/ls; secure; HttpOnly Persistent-Auth: true X-Powered-By: ASP.NET Date: Fri, 03 Jan 2014 19:43:14 GMT Content-Length: 5580 <html> <head> <title>Working...</title> </head> <body> <form method="POST" name="hiddenform" action="https://10.8.3.198:8043/SAML2WebBrowserPOSTHTTPS/login"> <input type="hidden" name="SAMLResponse" value="PHNhbWxwOlJlc3BvbnNlIElEPSJfNGQ5ZTFlNjctN2M1Yy00NjRlLTkxYWQtNzg3Mzg0MTBkYjUzIiBWZXJzaW9uPSIyLjAiIElzc3VlSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxNC4zOTFaIiBEZXN0aW5hdGlvbj0iaHR0cHM6Ly8xMC44LjMuMTk4OjgwNDMvU0FNTDJXZWJCcm93c2VyUG9zdEhUVFBTL2xvZ2luIiBDb25zZW50PSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6Y29uc2VudDp1bnNwZWNpZmllZCIgSW5SZXNwb25zZVRvPSJfNGRmODU4NDlhNTYyMzM0NTliYTRhY2Y2NzJmZmE1M2QiIHhtbG5zOnNhbWxwPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6cHJvdG9jb2wiPjxJc3N1ZXIgeG1sbnM9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphc3NlcnRpb24iPmh0dHA6Ly9DbGF5Lm1pNi5jb20vYWRmcy9zZXJ2aWNlcy90cnVzdDwvSXNzdWVyPjxzYW1scDpTdGF0dXM+PHNhbWxwOlN0YXR1c0NvZGUgVmFsdWU9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpzdGF0dXM6U3VjY2VzcyIgLz48L3NhbWxwOlN0YXR1cz48QXNzZXJ0aW9uIElEPSJfYTRlOTlhMDItNDEyMy00NWZmLWI5ZDUtN2NhZDNkNjUwMjIwIiBJc3N1ZUluc3RhbnQ9IjIwMTQtMDEtMDNUMTk6NDM6MTQuMzkxWiIgVmVyc2lvbj0iMi4wIiB4bWxucz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiI+PElzc3Vlcj5odHRwOi8vQ2xheS5taTYuY29tL2FkZnMvc2VydmljZXMvdHJ1c3Q8L0lzc3Vlcj48ZHM6U2lnbmF0dXJlIHhtbG5zOmRzPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjIj48ZHM6U2lnbmVkSW5mbz48ZHM6Q2Fub25pY2FsaXphdGlvbk1ldGhvZCBBbGdvcml0aG09Imh0dHA6Ly93d3cudzMub3JnLzIwMDEvMTAveG1sLWV4Yy1jMTRuIyIgLz48ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8wNC94bWxkc2lnLW1vcmUjcnNhLXNoYTI1NiIgLz48ZHM6UmVmZXJlbmNlIFVSST0iI19hNGU5OWEwMi00MTIzLTQ1ZmYtYjlkNS03Y2FkM2Q2NTAyMjAiPjxkczpUcmFuc2Zvcm1zPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjZW52ZWxvcGVkLXNpZ25hdHVyZSIgLz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIiAvPjwvZHM6VHJhbnNmb3Jtcz48ZHM6RGlnZXN0TWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8wNC94bWxlbmMjc2hhMjU2IiAvPjxkczpEaWdlc3RWYWx1ZT4rMzR3cERhbWlQd3BuT29QMjNsY3ZCRFg2dEtULzRoTHpCS3c3WmM1NmtzPTwvZHM6RGlnZXN0VmFsdWU+PC9kczpSZWZlcmVuY2U+PC9kczpTaWduZWRJbmZvPjxkczpTaWduYXR1cmVWYWx1ZT5kMVBQS2ViNlJaYUt6Ym05blFCVk5xcVQxNU1iUjFSSi9lSlRIci81WWlyeVdDdlBtWDNNZlE4bHFLbFZDNm92RWVMRG1jblJHSjdDLzI5U0dHMVVVYmwwWDgzMFc3QmQ0TjRxZlMyNVhJQ1ZwanQzTlQzendFWTFDYjJDQ1pKSWh1ZUdGcHFCMzFJb1RmZkxxZm9Ea0RJN3V0eUlOejRUTjBKcExLSjc5eUVBQ3UwaXBEbFJXQ2hlYVNyUmpOMURKWXUzYThiSVBjNk8xS0l6VStNU1lDY1lTTmxGVmpaKy90SjR2dXp2WVJUa0M2a3F2dDNJV2RnL1Vsa3EvNU5HUk12bVZEeUVsdlczRzhKeE5tMGJlRzBaYi9TR1hIV3lvekg2ZCtST0ZHYklHM1U2T0p4Sk41TzVJN2VndUNyekV5SDc0ZGtpeU8yM2wyNHJNd29UaEE9PTwvZHM6U2lnbmF0dXJlVmFsdWU+PEtleUluZm8geG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiPjxkczpYNTA5RGF0YT48ZHM6WDUwOUNlcnRpZmljYXRlPk1JSUMxRENDQWJ5Z0F3SUJBZ0lRRldpUitHNEVPcjFISy9hRlVac2ovREFOQmdrcWhraUc5dzBCQVFzRkFEQW1NU1F3SWdZRFZRUURFeHRCUkVaVElGTnBaMjVwYm1jZ0xTQkRiR0Y1TG0xcE5pNWpiMjB3SGhjTk1UTXdPREE0TVRZek9ESTFXaGNOTVRRd09EQTRNVFl6T0RJMVdqQW1NU1F3SWdZRFZRUURFeHRCUkVaVElGTnBaMjVwYm1jZ0xTQkRiR0Y1TG0xcE5pNWpiMjB3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQ2h6Nnp6RmFNVlhmbTNGTzdaK2xJWmV1ZU50MTdHdytMM0Y0ZjNOTm9RTi9YNUp2Ykh6dU1wQkhRRFVjWHVUUFE1N2M1T3JkK1hnQlZ3bDJlaGJncWRPWEw1YW5IUHhDcGtnQnpyV0VISW51VlM1WGVjYkFEMEVmdjhrdDNIcDIrSlVyRUY4NGFNcTRaeFB6S21LSU05V2x6OHJZNXVvVVJwZmZ4a0NRVFoyVWhpc0lubGthUmxOeVZIdm00TE4xV1lkbWtpbHdFUTV3dERXUHllNlBXNmpDSzhuVDR0czRVZHh4b0hSb0h0Tktwd3VqMHkrbmU4cnZ2TWtpUVBsT0lrbVJVa2hBMU9zZFlKNldhM0lJSlJwdzJIV20rMDJpTktIcmt3ZWd6L21CYy9HTmxnM0Y5Z3gxVzBxWllCMnYzV1BpUUNIZ0VWR0h0ai9MNkZYcTRyQWdNQkFBRXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBQnVlUm5QUkpoQnJ3eXl1b1d3UnlLNkp4TmpGem01ZkwxY3R3eGhtY2UreUJxaHRySnNpKzNNL1pqbVh0K3NHcnZQQk14RDNVUzYyZXhwenQ4V0NPNFltc1hmazdTSDczYWQrWVhlVWtuOEVXSUxGNEI0dkowYXdQdGxGcWJVVEVacDJlRSttT1pEVkpKekw1NHNLeHV4QXVxSUdmeVdacC9UK2VvRzJVcEErRDVYY1E4aHNQREN5MVczNFJMYkNkNUw0aFlNZ25ZNkMyTzVrL3I5bzhLdzRscmNlSGtYaTlOZ3JDVTd1KzAxdDRWQ3lBbTgyNWFLWitObmxGbk9nRG1tT1E1MS9JWDZ3dWx2d0JXeE95NmV6Rm9SZDAwNkp2dEUxUGIrc1JzbU9zc0pHUDFObUd0b09JZVJYNWF3STJJZVpkV1pVSjBOWGl1V2JDa1ZsNGJJPTwvZHM6WDUwOUNlcnRpZmljYXRlPjwvZHM6WDUwOURhdGE+PC9LZXlJbmZvPjwvZHM6U2lnbmF0dXJlPjxTdWJqZWN0PjxTdWJqZWN0Q29uZmlybWF0aW9uIE1ldGhvZD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmNtOmJlYXJlciI+PFN1YmplY3RDb25maXJtYXRpb25EYXRhIEluUmVzcG9uc2VUbz0iXzRkZjg1ODQ5YTU2MjMzNDU5YmE0YWNmNjcyZmZhNTNkIiBOb3RPbk9yQWZ0ZXI9IjIwMTQtMDEtMDNUMTk6NDg6MTQuMzkxWiIgUmVjaXBpZW50PSJodHRwczovLzEwLjguMy4xOTg6ODA0My9TQU1MMldlYkJyb3dzZXJQb3N0SFRUUFMvbG9naW4iIC8+PC9TdWJqZWN0Q29uZmlybWF0aW9uPjwvU3ViamVjdD48Q29uZGl0aW9ucyBOb3RCZWZvcmU9IjIwMTQtMDEtMDNUMTk6NDM6MTQuMzkwWiIgTm90T25PckFmdGVyPSIyMDE0LTAxLTAzVDIwOjQzOjE0LjM5MFoiPjxBdWRpZW5jZVJlc3RyaWN0aW9uPjxBdWRpZW5jZT5odHRwczovLzEwLjguMy4xOTg6ODA0MzwvQXVkaWVuY2U+PC9BdWRpZW5jZVJlc3RyaWN0aW9uPjwvQ29uZGl0aW9ucz48QXR0cmlidXRlU3RhdGVtZW50PjxBdHRyaWJ1dGUgTmFtZT0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93cy8yMDA4LzA2L2lkZW50aXR5L2NsYWltcy93aW5kb3dzYWNjb3VudG5hbWUiPjxBdHRyaWJ1dGVWYWx1ZT5NSTZcQWRtaW5pc3RyYXRvcjwvQXR0cmlidXRlVmFsdWU+PC9BdHRyaWJ1dGU+PC9BdHRyaWJ1dGVTdGF0ZW1lbnQ+PEF1dGhuU3RhdGVtZW50IEF1dGhuSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxNC4zNThaIj48QXV0aG5Db250ZXh0PjxBdXRobkNvbnRleHRDbGFzc1JlZj51cm46ZmVkZXJhdGlvbjphdXRoZW50aWNhdGlvbjp3aW5kb3dzPC9BdXRobkNvbnRleHRDbGFzc1JlZj48L0F1dGhuQ29udGV4dD48L0F1dGhuU3RhdGVtZW50PjwvQXNzZXJ0aW9uPjwvc2FtbHA6UmVzcG9uc2U+" /> <input type="hidden" name="RelayState" value="12f6b8be-72e9-4bb9-97a1-4392f2746ecd" /> <noscript> <p> Script is disabled. Click Submit to continue. </p> <input type="submit" value="Submit" /> </noscript> </form> <script language="javascript"> window.setTimeout('document.forms[0].submit()', 0); </script> </body> </html>
The Base64 encoded SAML <AuthnResponse> message for step 4, when decoded, is as follows:
<samlp:Response ID="_4d9e1e67-7c5c-464e-91ad-78738410db53" Version="2.0" IssueInstant="2014-01-03T19:43:14.391Z" Destination="https://10.8.3.198:8043/SAML2WebBrowserPOSTHTTPS/login" Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" InResponseTo="_4df85849a56233459ba4acf672ffa53d" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"> <Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion"> http://cic.example.com/adfs/services/trust </Issuer> <samlp:Status> <samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" /> </samlp:Status> <Assertion ID="_a4e99a02-4123-45ff-b9d5-7cad3d650220" IssueInstant="2014-01-03T19:43:14.391Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:assertion"> <Issuer> http://cic.example.com/adfs/services/trust </Issuer> <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" /> <ds:Reference URI="#_a4e99a02-4123-45ff-b9d5-7cad3d650220"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" /> <ds:DigestValue> +34wpDamiPwpnOoP23lcvBDX6tKT/4hLzBKw7Zc56ks= </ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue> d1PPKeb6RZaKzbm9nQBVNqqT15MbR1RJ/eJTHr/5YiryWCvPmX3MfQ8lqKlVC6ovEeLDmcnRGJ7C/29SGG1UUbl0X830W7Bd4N4qfS25XICVpjt3NT3zwEY1Cb2CCZJIhueGFpqB31IoTffLqfoDkDI7utyINz4TN0JpLKJ79yEACu0ipDlRWCheaSrRjN1DJYu3a8bIPc6O1KIzU+MSYCcYSNlFVjZ+/tJ4vuzvYRTkC6kqvt3IWdg/Ulkq/5NGRMvmVDyElvW3G8JxNm0beG0Zb/SGXHWyozH6d+ROFGbIG3U6OJxJN5O5I7eguCrzEyH74dkiyO23l24rMwoThA== </ds:SignatureValue> <KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#"> <ds:X509Data> <ds:X509Certificate> MIIC1DCCAbygAwIBAgIQFWiR+G4EOr1HK/aFUZsj/DANBgkqhkiG9w0BAQsFADAmMSQwIgYDVQQDExtBREZTIFNpZ25pbmcgLSBDbGF5Lm1pNi5jb20wHhcNMTMwODA4MTYzODI1WhcNMTQwODA4MTYzODI1WjAmMSQwIgYDVQQDExtBREZTIFNpZ25pbmcgLSBDbGF5Lm1pNi5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQChz6zzFaMVXfm3FO7Z+lIZeueNt17Gw+L3F4f3NNoQN/X5JvbHzuMpBHQDUcXuTPQ57c5Ord+XgBVwl2ehbgqdOXL5anHPxCpkgBzrWEHInuVS5XecbAD0Efv8kt3Hp2+JUrEF84aMq4ZxPzKmKIM9Wlz8rY5uoURpffxkCQTZ2UhisInlkaRlNyVHvm4LN1WYdmkilwEQ5wtDWPye6PW6jCK8nT4ts4UdxxoHRoHtNKpwuj0y+ne8rvvMkiQPlOIkmRUkhA1OsdYJ6Wa3IIJRpw2HWm+02iNKHrkwegz/mBc/GNlg3F9gx1W0qZYB2v3WPiQCHgEVGHtj/L6FXq4rAgMBAAEwDQYJKoZIhvcNAQELBQADggEBABueRnPRJhBrwyyuoWwRyK6JxNjFzm5fL1ctwxhmce+yBqhtrJsi+3M/ZjmXt+sGrvPBMxD3US62expzt8WCO4YmsXfk7SH73ad+YXeUkn8EWILF4B4vJ0awPtlFqbUTEZp2eE+mOZDVJJzL54sKxuxAuqIGfyWZp/T+eoG2UpA+D5XcQ8hsPDCy1W34RLbCd5L4hYMgnY6C2O5k/r9o8Kw4lrceHkXi9NgrCU7u+01t4VCyAm825aKZ+NnlFnOgDmmOQ51/IX6wulvwBWxOy6ezFoRd006JvtE1Pb+sRsmOssJGP1NmGtoOIeRX5awI2IeZdWZUJ0NXiuWbCkVl4bI= </ds:X509Certificate> </ds:X509Data> </KeyInfo> </ds:Signature> <Subject> <SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <SubjectConfirmationData InResponseTo="_4df85849a56233459ba4acf672ffa53d" NotOnOrAfter="2014-01-03T19:48:14.391Z" Recipient="https://10.8.3.198:8043/SAML2WebBrowserPOSTHTTPS/login" /> </SubjectConfirmation> </Subject> <Conditions NotBefore="2014-01-03T19:43:14.390Z" NotOnOrAfter="2014-01-03T20:43:14.390Z"> <AudienceRestriction> <Audience> https://10.8.3.198:8043 </Audience> </AudienceRestriction> </Conditions> <AttributeStatement> <Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"> <AttributeValue> MI6\Administrator </AttributeValue> </Attribute> </AttributeStatement> <AuthnStatement AuthnInstant="2014-01-03T19:43:14.358Z"> <AuthnContext> <AuthnContextClassRef> urn:federation:authentication:windows </AuthnContextClassRef> </AuthnContext> </AuthnStatement> </Assertion> </samlp:Response>
-
The user agent posts the SAML <AuthnResponse> message to the secure token server:
POST /SAML2WebBrowserPOSTHTTPS/login HTTP/1.1 Host: 10.8.3.198:8043 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: https://cic.example.com/adfs/ls/auth/integrated/ Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 5155 SAMLResponse=PHNhbWxwOlJlc3BvbnNlIElEPSJfNGQ5ZTFlNjctN2M1Yy00NjRlLTkxYWQtNzg3Mzg0MTBkYjUzIiBWZXJzaW9uPSIyLjAiIElzc3VlSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxNC4zOTFaIiBEZXN0aW5hdGlvbj0iaHR0cHM6Ly8xMC44LjMuMTk4OjgwNDMvU0FNTDJXZWJCcm93c2VyUG9zdEhUVFBTL2xvZ2luIiBDb25zZW50PSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6Y29uc2VudDp1bnNwZWNpZmllZCIgSW5SZXNwb25zZVRvPSJfNGRmODU4NDlhNTYyMzM0NTliYTRhY2Y2NzJmZmE1M2QiIHhtbG5zOnNhbWxwPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6cHJvdG9jb2wiPjxJc3N1ZXIgeG1sbnM9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDphc3NlcnRpb24iPmh0dHA6Ly9DbGF5Lm1pNi5jb20vYWRmcy9zZXJ2aWNlcy90cnVzdDwvSXNzdWVyPjxzYW1scDpTdGF0dXM%2BPHNhbWxwOlN0YXR1c0NvZGUgVmFsdWU9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpzdGF0dXM6U3VjY2VzcyIgLz48L3NhbWxwOlN0YXR1cz48QXNzZXJ0aW9uIElEPSJfYTRlOTlhMDItNDEyMy00NWZmLWI5ZDUtN2NhZDNkNjUwMjIwIiBJc3N1ZUluc3RhbnQ9IjIwMTQtMDEtMDNUMTk6NDM6MTQuMzkxWiIgVmVyc2lvbj0iMi4wIiB4bWxucz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiI%2BPElzc3Vlcj5odHRwOi8vQ2xheS5taTYuY29tL2FkZnMvc2VydmljZXMvdHJ1c3Q8L0lzc3Vlcj48ZHM6U2lnbmF0dXJlIHhtbG5zOmRzPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjIj48ZHM6U2lnbmVkSW5mbz48ZHM6Q2Fub25pY2FsaXphdGlvbk1ldGhvZCBBbGdvcml0aG09Imh0dHA6Ly93d3cudzMub3JnLzIwMDEvMTAveG1sLWV4Yy1jMTRuIyIgLz48ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8wNC94bWxkc2lnLW1vcmUjcnNhLXNoYTI1NiIgLz48ZHM6UmVmZXJlbmNlIFVSST0iI19hNGU5OWEwMi00MTIzLTQ1ZmYtYjlkNS03Y2FkM2Q2NTAyMjAiPjxkczpUcmFuc2Zvcm1zPjxkczpUcmFuc2Zvcm0gQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwLzA5L3htbGRzaWcjZW52ZWxvcGVkLXNpZ25hdHVyZSIgLz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIiAvPjwvZHM6VHJhbnNmb3Jtcz48ZHM6RGlnZXN0TWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8wNC94bWxlbmMjc2hhMjU2IiAvPjxkczpEaWdlc3RWYWx1ZT4rMzR3cERhbWlQd3BuT29QMjNsY3ZCRFg2dEtULzRoTHpCS3c3WmM1NmtzPTwvZHM6RGlnZXN0VmFsdWU%2BPC9kczpSZWZlcmVuY2U%2BPC9kczpTaWduZWRJbmZvPjxkczpTaWduYXR1cmVWYWx1ZT5kMVBQS2ViNlJaYUt6Ym05blFCVk5xcVQxNU1iUjFSSi9lSlRIci81WWlyeVdDdlBtWDNNZlE4bHFLbFZDNm92RWVMRG1jblJHSjdDLzI5U0dHMVVVYmwwWDgzMFc3QmQ0TjRxZlMyNVhJQ1ZwanQzTlQzendFWTFDYjJDQ1pKSWh1ZUdGcHFCMzFJb1RmZkxxZm9Ea0RJN3V0eUlOejRUTjBKcExLSjc5eUVBQ3UwaXBEbFJXQ2hlYVNyUmpOMURKWXUzYThiSVBjNk8xS0l6VStNU1lDY1lTTmxGVmpaKy90SjR2dXp2WVJUa0M2a3F2dDNJV2RnL1Vsa3EvNU5HUk12bVZEeUVsdlczRzhKeE5tMGJlRzBaYi9TR1hIV3lvekg2ZCtST0ZHYklHM1U2T0p4Sk41TzVJN2VndUNyekV5SDc0ZGtpeU8yM2wyNHJNd29UaEE9PTwvZHM6U2lnbmF0dXJlVmFsdWU%2BPEtleUluZm8geG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiPjxkczpYNTA5RGF0YT48ZHM6WDUwOUNlcnRpZmljYXRlPk1JSUMxRENDQWJ5Z0F3SUJBZ0lRRldpUitHNEVPcjFISy9hRlVac2ovREFOQmdrcWhraUc5dzBCQVFzRkFEQW1NU1F3SWdZRFZRUURFeHRCUkVaVElGTnBaMjVwYm1jZ0xTQkRiR0Y1TG0xcE5pNWpiMjB3SGhjTk1UTXdPREE0TVRZek9ESTFXaGNOTVRRd09EQTRNVFl6T0RJMVdqQW1NU1F3SWdZRFZRUURFeHRCUkVaVElGTnBaMjVwYm1jZ0xTQkRiR0Y1TG0xcE5pNWpiMjB3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQ2h6Nnp6RmFNVlhmbTNGTzdaK2xJWmV1ZU50MTdHdytMM0Y0ZjNOTm9RTi9YNUp2Ykh6dU1wQkhRRFVjWHVUUFE1N2M1T3JkK1hnQlZ3bDJlaGJncWRPWEw1YW5IUHhDcGtnQnpyV0VISW51VlM1WGVjYkFEMEVmdjhrdDNIcDIrSlVyRUY4NGFNcTRaeFB6S21LSU05V2x6OHJZNXVvVVJwZmZ4a0NRVFoyVWhpc0lubGthUmxOeVZIdm00TE4xV1lkbWtpbHdFUTV3dERXUHllNlBXNmpDSzhuVDR0czRVZHh4b0hSb0h0Tktwd3VqMHkrbmU4cnZ2TWtpUVBsT0lrbVJVa2hBMU9zZFlKNldhM0lJSlJwdzJIV20rMDJpTktIcmt3ZWd6L21CYy9HTmxnM0Y5Z3gxVzBxWllCMnYzV1BpUUNIZ0VWR0h0ai9MNkZYcTRyQWdNQkFBRXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBQnVlUm5QUkpoQnJ3eXl1b1d3UnlLNkp4TmpGem01ZkwxY3R3eGhtY2UreUJxaHRySnNpKzNNL1pqbVh0K3NHcnZQQk14RDNVUzYyZXhwenQ4V0NPNFltc1hmazdTSDczYWQrWVhlVWtuOEVXSUxGNEI0dkowYXdQdGxGcWJVVEVacDJlRSttT1pEVkpKekw1NHNLeHV4QXVxSUdmeVdacC9UK2VvRzJVcEErRDVYY1E4aHNQREN5MVczNFJMYkNkNUw0aFlNZ25ZNkMyTzVrL3I5bzhLdzRscmNlSGtYaTlOZ3JDVTd1KzAxdDRWQ3lBbTgyNWFLWitObmxGbk9nRG1tT1E1MS9JWDZ3dWx2d0JXeE95NmV6Rm9SZDAwNkp2dEUxUGIrc1JzbU9zc0pHUDFObUd0b09JZVJYNWF3STJJZVpkV1pVSjBOWGl1V2JDa1ZsNGJJPTwvZHM6WDUwOUNlcnRpZmljYXRlPjwvZHM6WDUwOURhdGE%2BPC9LZXlJbmZvPjwvZHM6U2lnbmF0dXJlPjxTdWJqZWN0PjxTdWJqZWN0Q29uZmlybWF0aW9uIE1ldGhvZD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmNtOmJlYXJlciI%2BPFN1YmplY3RDb25maXJtYXRpb25EYXRhIEluUmVzcG9uc2VUbz0iXzRkZjg1ODQ5YTU2MjMzNDU5YmE0YWNmNjcyZmZhNTNkIiBOb3RPbk9yQWZ0ZXI9IjIwMTQtMDEtMDNUMTk6NDg6MTQuMzkxWiIgUmVjaXBpZW50PSJodHRwczovLzEwLjguMy4xOTg6ODA0My9TQU1MMldlYkJyb3dzZXJQb3N0SFRUUFMvbG9naW4iIC8%2BPC9TdWJqZWN0Q29uZmlybWF0aW9uPjwvU3ViamVjdD48Q29uZGl0aW9ucyBOb3RCZWZvcmU9IjIwMTQtMDEtMDNUMTk6NDM6MTQuMzkwWiIgTm90T25PckFmdGVyPSIyMDE0LTAxLTAzVDIwOjQzOjE0LjM5MFoiPjxBdWRpZW5jZVJlc3RyaWN0aW9uPjxBdWRpZW5jZT5odHRwczovLzEwLjguMy4xOTg6ODA0MzwvQXVkaWVuY2U%2BPC9BdWRpZW5jZVJlc3RyaWN0aW9uPjwvQ29uZGl0aW9ucz48QXR0cmlidXRlU3RhdGVtZW50PjxBdHRyaWJ1dGUgTmFtZT0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93cy8yMDA4LzA2L2lkZW50aXR5L2NsYWltcy93aW5kb3dzYWNjb3VudG5hbWUiPjxBdHRyaWJ1dGVWYWx1ZT5NSTZcQWRtaW5pc3RyYXRvcjwvQXR0cmlidXRlVmFsdWU%2BPC9BdHRyaWJ1dGU%2BPC9BdHRyaWJ1dGVTdGF0ZW1lbnQ%2BPEF1dGhuU3RhdGVtZW50IEF1dGhuSW5zdGFudD0iMjAxNC0wMS0wM1QxOTo0MzoxNC4zNThaIj48QXV0aG5Db250ZXh0PjxBdXRobkNvbnRleHRDbGFzc1JlZj51cm46ZmVkZXJhdGlvbjphdXRoZW50aWNhdGlvbjp3aW5kb3dzPC9BdXRobkNvbnRleHRDbGFzc1JlZj48L0F1dGhuQ29udGV4dD48L0F1dGhuU3RhdGVtZW50PjwvQXNzZXJ0aW9uPjwvc2FtbHA6UmVzcG9uc2U%2B&RelayState=12f6b8be-72e9-4bb9-97a1-4392f2746ecd
-
The secure token server issues the user agent an ININ-STS-TOKEN:
HTTP/1.1 200 OK ININ-STS-TOKEN: (3"ExpirationTime"T20140117194314.989423,"IdentityProvider""12f6b8be-72e9-4bb9-97a1-4392f2746ecd","AuthenticationType""SAML2WebBrowserPOSTHTTPS")|Js4dizHlKCwE88R60KKrCi49udulzSkNRKmxKb6P0fphF9jZz/gudeZ4gQ+4kOztj4OvYELeLJYuwSwGS+F4TZgBxJOMc3Wkq8s3cO2QwaBVxgWPt1vMVCeJ3AHwRBuUW5Y0JGvInGwvsW9pJnzY5CxyYDyBKJLe0J9z8mHNnhjoIeHd/BjMYPqVMg9x10wY/dXhXa+GM3O3bZuyGRMzNrW/Vm8J/+mv8N8+2nT9Gxq2hMZGkFhfavaM7EJfYZjInLKep26zZOGwf2tR3bnYICbcLMdrwyTj1jqiHSl0QryiipHGf+eCSEoJxxuabA130xQoFHahzz7NdzspYucpDQ== Date: Fri, 03 Jan 2014 19:43:15 GMT Server: I3STSCore Content-Length: 0



