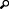- Contents
Log Viewer Help
Logged Columns
The table below describes columns in a log file. To control the visibility and order of columns, see Manage Columns in the Message List.
Icon
Icons describe the type of log message. The icons are:
Message
The message text.
Timestamp
The time when the message was logged, in hh:mm:ss:mmm_nnnn format. This notation stands for hours, minutes, seconds, milliseconds, and nanoseconds, in up to 9 digits of precision. However, time slices smaller than 15 ms have little meaning, since the overhead of the operating system must be considered. Timestamps are also incremented using series numbers to relate entries within a time span.
Topic
The routines that write log messages are called trace topics. Trace topics correspond to subroutines invoked by a subsystem, or to some type of major functionality provided by an application. Every subsystem and application has its own set of trace topics.
Level
Each topic has a numeric trace level setting that controls the verbosity of messages written about that topic. Not all messages are equally important. Messages from some routines are more important than others.
Trace levels are sometimes called topic levels, since people tend to combine both terms. Topic is what is traced, level controls how much. Trace levels are numeric values that determine which messages are logged for a topic, based upon the severity of the message.
Thread
Threads are the basic unit to which an operating system allocates processor time. A thread is code that is to be serially executed within a process and more than one thread can be executing code inside a process. Each thread maintains exception handlers, a scheduling priority, and a set of structures the system uses to save the thread context until it is scheduled. The thread context includes all of the information the thread needs to seamlessly resume execution, including the thread's set of CPU registers and stack, in the address space of the thread's host process.
Type
The Type column is the textual equivalent of the Icon column. The message types are Start Tracing, Stop Tracing, Note, Warning, Error, Enter Scope, Exit Scope, Object Construction, and Object Destruction.
Subsystem
The name of the CIC subsystem that wrote the log entry. The Interaction Center platform is composed of software components, called subsystems. These components are written in the C++ language to maximize performance. Individual subsystems are coordinated by a central communication hub known as the Notifier.
Call Level
Call Level (or call stack, if you prefer) is an indicator of functions calling other functions. The first calling function is level 0. If the main function calls a helper function, the helper is considered to be at call level 1, and so forth. Call levels help trace the flow of control from one function to another.
In Exception
This Boolean flag is True when if the module was in an exception handler when the message was logged. Since exceptions alter a program's flow of control, this flag helps indicate that customary statements may not have been written due to an exception.
Function
Function indicates the name of the source code subroutine (called function) that wrote the log entry, in the form: Library:Class:Subroutine. For example: DispatcherLib::JobWaitlist::EnqueueJob()
Filename
The path to the source code file in the code management system.
Line #
The line number in the source code file that corresponds to the message entry.
Trust Level
The level of trust assigned to an assembly, which affects what system resources the function had access to.
Logfile
The fully qualified path to the log file.
Encryption Key Id
This column displays the string that was used to encrypt a portion of the log entry. Logs are not encrypted, but some log elements in a log (passwords for example) can be encrypted by a subsystem. Here's what an encrypted log entry looks like:
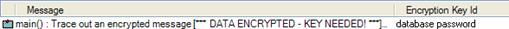
Encryption key Id is a string that indicates which key should be used to decrypt. For example, the Encryption Key Id might be "login password" or "database password". To decrypt the entry, the user would have to enter the appropriate password for the user account or database.
In this example, the encrypted portion of the message is displayed as [*** DATA ENCRYPTED - KEY NEEDED! ***], and the Encryption Key Id is "database password".
The topic titled Decrypt a log message explains how to decode messages.
Thread Name
The name of the thread, if the thread has a name.
This pointer
The pointer to a data structure internal to the code. If you are operating on a function that is part of a data object, this pointer indicates which data object.
Dynamically Assigned Columns
You may see columns other than those that are listed here. Some columns are dynamically defined for a particular type of log, if the column has meaning only in the context of that log type.