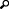- Contents
CX Insights Installation and Configuration Guide
Install CX Insights server
- Install RHEL version 8.3, 8.4 or 8.5 on either a physical or virtual server that meets the minimum requirements for the production environment. For more information about minimum requirements, see CX Insights server requirements.
- Download CX Insights Docker containers from the following website:
https://help.genesys.com/utilities-and-downloads.html
- Extract the CX Insights artifacts archive that contains ansible_install.sh, and cx-insights.tgz.
- Run the shell script ansible_install.sh to install the dependencies like Python, Ansible packages using the root user account. It also creates the CX Insights user account to perform all the Ansible roles and tasks.
Notes:
-
If the RHEL already has pip installed, then ensure that pip is of version 21.3.1, which is compatible with Python 3.9.0 else all the installation will fail.
-
By using the command which ansible, verify if Ansible is installed. If it is installed, you can see the Ansible version 2.9.27 and can also verify by running ansible -version command. Otherwise, rerun the ansible_install shell script.
-
By using the command cut -d: -f1 /etc/paswd and logging into CX Insights account, verify if CX Insights account is created.
-
su cxinsights
- Prerequisite for running Ansible-playbook
-
Extract the cxinsights-playbook-k3s file to the CX Insights user home directory. After extraction, move the kube_archive_clean.py file to the /home/cxinsights directory.
-
Generate Ansible vault for CX Insights user password. Ansible modules require this value to install k3s, helm.
- Ansible-vault encrypt_string 'passwd' --name 'helm_linux_host_passwd' --vault-id cxinsights@prompt, replace passwd with CX Insights user account password. It asks for the password for vault usage, enter the password and make a note of it, so that the user can enter the same password while running ansible-playbook command
- Ansible-vault encrypt_string 'passwd' --name 'tiller_linux_host_passwd' --vault-id cxinsights@prompt, generate the password again only if you are planning to keep controller and CX Insights server separately, else add the above generated vault value in both helm_linux_host_passwd and till_linux_host_passwd in the group_vars/all.yml file as shown below
-
Configure a backup directory and a cron job expression using the following parameters in the group_vars/all.yml file to backup CX Insights data.
-
backup_dir – specify the backup directory path. Configuring backup_dir is mandatory. For backup purposes, create the backup directory as a share path on a remote computer and mount the same on the local computer where you installed the CX Insights server. Example, /mnt/nfs/share/gcxibackup
-
cron_schedule – specify the cron expression that defines the backup frequency in which the backup activity runs. Configuring cron_schedule is optional. If you do not define any expression, the backup activity runs at the default time every day, that is at 12.00 am. An example cron expression to run the backup activity every day at 7.00 am and 12.00 pm looks like: "0 7,12 * * *". Note that Cron job is added for the root user only.
You can also restore the backed-up data at a future date when there is a system failure. For more information about restore, see Backup and restore configuration topic.
-
Specify the Genesys CX Insights (gcxi) properties in the values.yml file by referring to the following table:
|
Property name |
Description |
|---|---|
|
cicServerName |
The IP address of the primary CIC server. |
|
cicBackUpServerName |
The IP address of the secondary CIC server. |
|
langs (optional) |
The localization language required for your organization. Configuring langs is optional. The US English (en_US) is mandatory. You can also specify other supported languages of your choice along with en_US. Currently, the supported language pack values are: en-US,fr-FR,de-DE,ja-JP,pt-BR,es-ES,zh-CN,nl-NL,pl-PL For more information about the language pack configuration, see the sample configuration given below this table. |
|
certICSAML |
Specify the certificate details required for SAML authentication. Copy the contents of the certificate details from the ICSecureTokenServerCertificate.cer file in the CIC Server IC-Token Service folder (I3\IC\Certificates\ICSecureTokenServer\Default\ICSecureTokenServerCertificate.cer) and paste it here. |
|
mstrLicense |
Specify the Microstrategy License key. |
|
proxyEndpoint |
Specify the Fully Qualified Domain Name (FQDN) of a proxy server if the CX Insights server is accessed through a proxy server. If a proxy server is not configured in your environment, then you must specify the FQDN of the CX Insights server. |
|
secret |
Secret used for web socket authentication between the Analytics bridge and the microservices (mstrdataadapterserver and mstrtconnector). Ensure that the secret given here and the secret given in Interaction Administrator > System Configuration > Analytics > Configuration are same. |
|
Global variables |
|
|
tz |
Specify the time zone of the region where gcxi server is installed. |
|
hosts |
The Linux host name of the CX Insights server. Note that the host name you specify here must be an FQDN. |
|
maxPoolSize (optional) |
The maximum number of concurrent web sessions allowed. This is an optional parameter and the default value is 200. |
|
tls (ingress) |
Note: If you enable TLS, you must install an SSL certificate by following the Install SSL certificate on CIC server procedure. |
|
secret name (ingress) |
Specify the Kubernetes cluster secret. We recommend that you keep the secret name value as given in the values.yml file, that is, pcn-cxinsights-tls |
|
hosts (ingress) |
Specify the FQDN of ingress host. Typically, this is the FQDN of the CX Insights server that you configure in the hosts setting. |
|
tls (prometheusIngress) |
Note: If you enable TLS, you must install an SSL certificate by following the Install SSL certificate on CIC server procedure. |
|
secret name (prometheusIngress) |
Specify the Kubernetes cluster secret. We recommend that you keep the secret name value as given in the values.yml file, that is, pcn-cxinsights-tls |
|
hosts (prometheusIngress) |
Specify the FQDN of Prometheus ingress host. Typically, this is the FQDN of the CX Insights server that you configure in the hosts setting. |
Sample values.yml file configuration:
gcxi:
gcxiproperties:
cicServerName: IP address of primary IC server
cicBackUpServerName: IP address of secondary IC server
langs: en-US,fr-FR,de-DE,ja-JP,pt-BR,es-ES,zh-CN,nl-NL,pl-PL
maxPoolSize: 250
certICSAML:
MIIDoTCCAomgAwIBAgIFQWCBgwkwDQYJKoZIhvcNAQEFBQAwRzEQMA4GA1UECgwH
U2VydmVyczEVMBMGA1UECwwMU2VydmVyIEdyb3VwMRwwGgYDVQQDDBNPbHltcGlh
LmRldjIwMDAuY29tMB4XDTIwMDMwNzIxNDQ0M1oXDTQwMDMwODIxNDQ0M1owRzEQ
MA4GA1UECgwHU2VydmVyczEVMBMGA1UECwwMU2VydmVyIEdyb3VwMRwwGgYDVQQD
DBNPbHltcGlhLmRldjIwMDAuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB
CgKCAQEAs9WJ+2CqWRvQZs2SHc3kf/Ia+fOxW44SDgHxEMHKIqHx0rXwmuGbqTTt
mstrLicense: mstr license key
proxyEndpoint:
- pcn-rhel8.testCXI.com
secret: analytics
global:
tz: America/Indiana/Indianapolis
hosts:
- pcn-rhel8.testCXI.com
ingress:
tls:
- secretName: pcn-cxinsights-tls
hosts:
- pcn-rhel8.testCXI.com
prometheusIngress:
tls:
- secretName: pcn-cxinsights-tls
hosts:
- pcn-rhel8.testCXI.com
-
Below is the inventory.yml file in the cxinsights-playbook-k3s directory, specify with appropriate values. For example: Assume Ansible and k3s are running on the same machine. If the controller is different from target machine, then helm_linux_host should be the controller host FQDN and tiller-linux-host should be the FQDN of the CX Insights server host.
---
helm_linux_host:
hosts:
xxx-xxxxx-xxxxx.xxxxxxx.com
vars:
ansible_user: '{{ user }}'
ansible_ssh_pass: '{{ passwd }}'
tiller_linux_host:
hosts:
xxx-xxxxx-xxxxx.xxxxxxx.com
vars:
ansible_user: '{{ user }}'
ansible_ssh_pass: '{{ passwd }}'
-
If this is the fresh installation and you want to save the application data in secondary partition, keep the default value of data_dir as given in the main.yml file. The default value of data_dir is /home/cxinsights/kube_data. If you are already using the primary partition, modify the data_dir value in the main.yml file as shown below.
data_dir: ''
Note: If this is the fresh installation of CX Insights, we recommend that you deploy the software in secondary partition, provided you have the disk space as recommended in step 1. Drive partitioning and using secondary drive to save CX Insights data is possible only for fresh installation. If CX Insights is already installed without partitioning the drive, you may not be able to use the secondary drive. In that case you must modify data_dir as ' '.
- Run the Ansible Playbook to start the services on the CX Insights server. For the first time, it is slow as dependencies get installed.
sudo ansible-playbook --vault-id cxinsights@prompt -i inventory.yml site.yml -K
Note:
- Make sure you enter CX Insights password when BECOME password is asked.
- After the deployment is triggered, you must wait for some time until the state of GCXI pod is healthy.
-
Run the below mentioned commands to ensure that everything is up and running.
-
To see all the containers are up and running in all namespaces, use the command kubect1 get pods -A
-
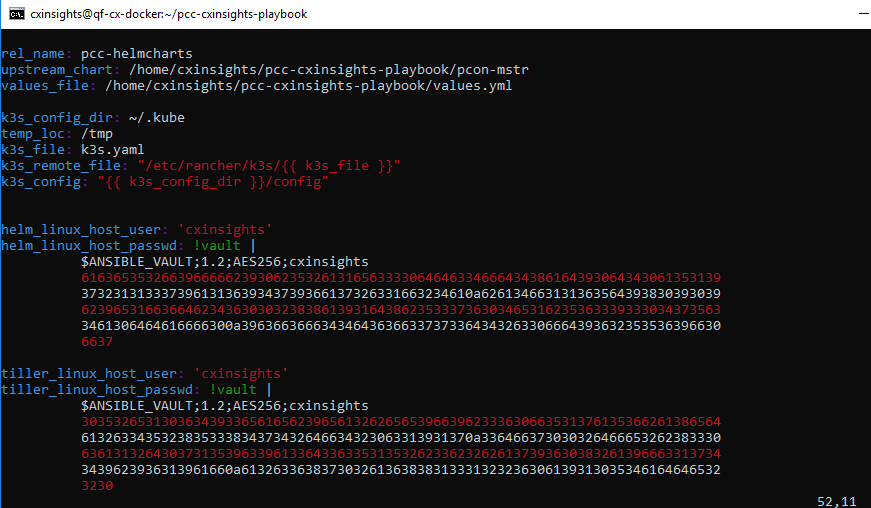
To see all the containers are up and running only in pcn-cxinsights-system namespace, use the command kubectl get pods --namespace=pcn-cxinsights-system
-
To see all the services running in all namespaces, use the command kubectl get services -A
-
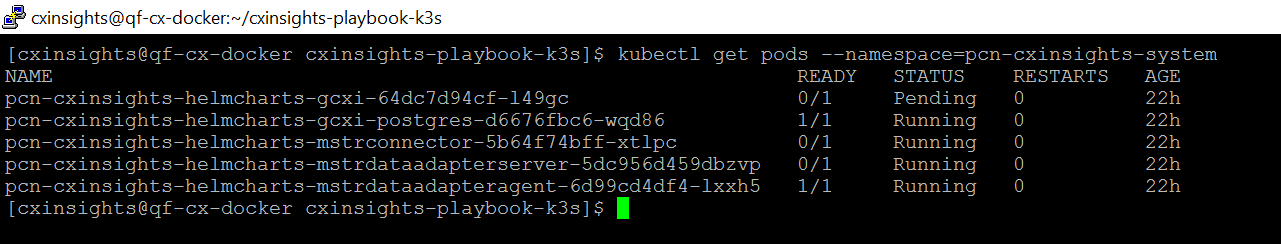
To see all the services are running only in pcn-cxinsights-system namespace, use the command kubectl get services --namespace=pcn-cxinsights-system
-
To see all the persistent volumes in all namespaces, use the command kubectl get pvc -A
-
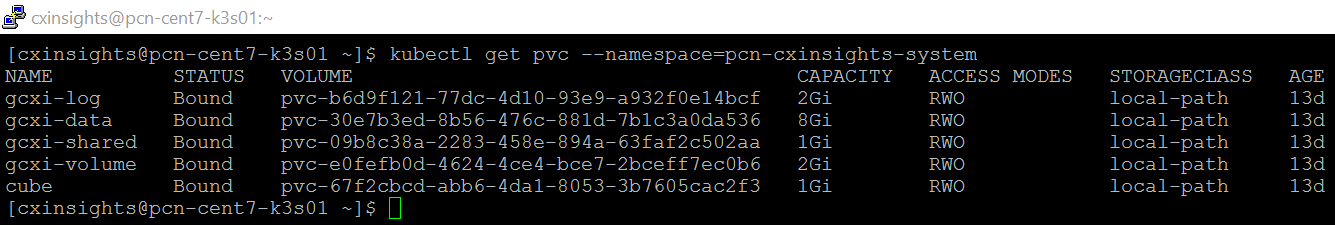
To see all the persistent volumes only in pcn-cxinsights-system namespace, use the command kubectl get pvc --namespace=pcn-cxinsights-system
Related Topics:
Install SSL certificate on CIC server
Configure CX Insights in Interaction Administrator
Backup and restore configuration